TL;DR
- Companies need to detect VPN traffic to prevent bypassing local laws like Texas HB1181 and Florida HB3
- There are 2 major methods to detecting VPN traffic today:
- Static IP list based detections
- Inspecting indicators of VPN traffic at the network level
- Static IP lists are cheap, and can be effective to some degree
- Inspecting indicators of VPN infrastructure cover much more ground
- Detecting VPN traffic is a cat-and-mouse game, so settling for quick and dirty will not protect your business

Why VPN detection matters in 2026
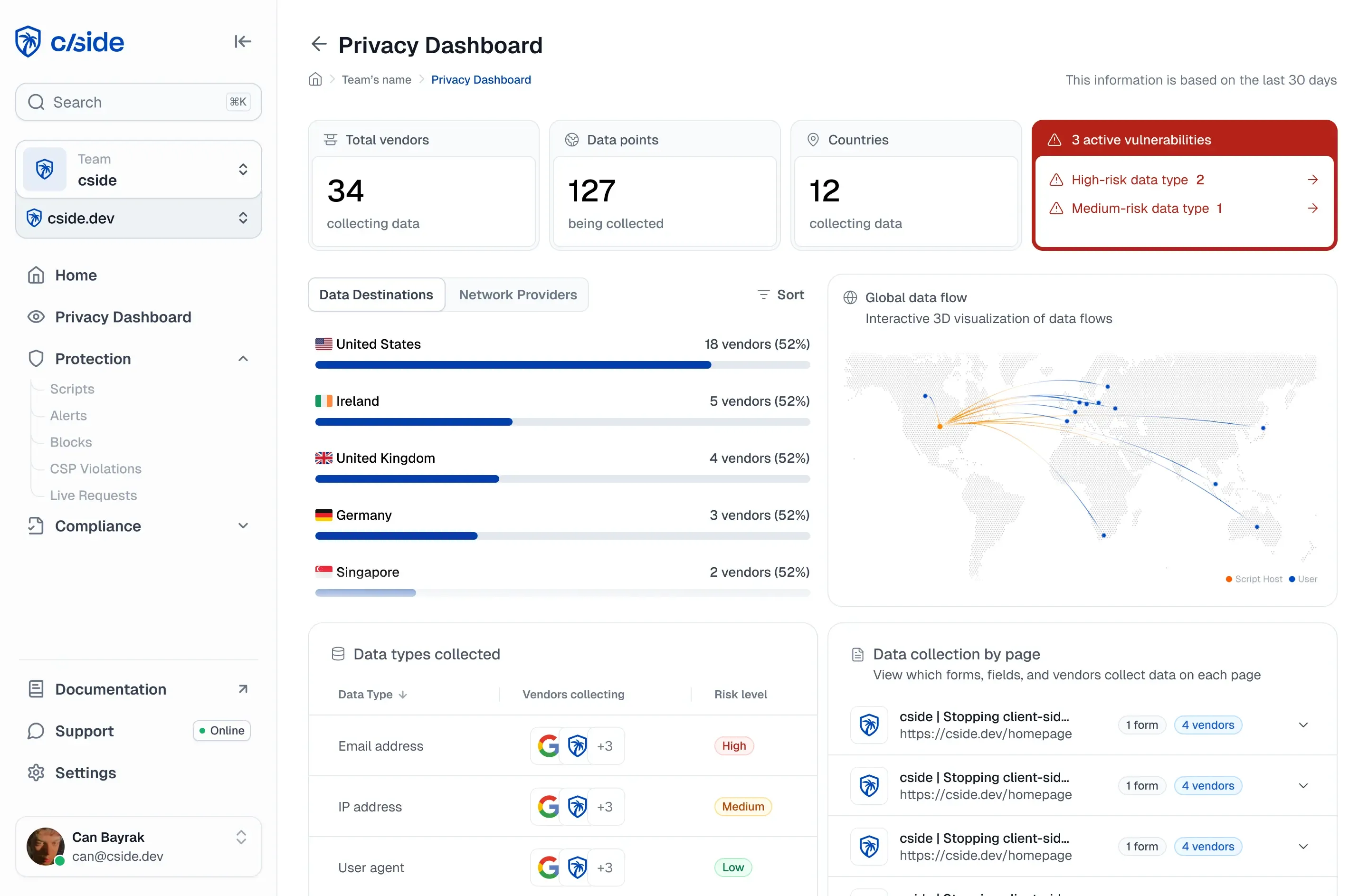
VPN detection has evolved from a niche technical challenge to a business imperative. As age verification laws sweep across US states and the UK Online Safety Act takes effect, website owners now face legal liability when minors access restricted content, even if those web visitors use VPNs to bypass geographic restrictions.
From Texas to Wisconsin to the United Kingdom, the message from legislators is clear: detecting and managing VPN traffic is your responsibility. In this blogpost we'll examine why VPN detection matters, review the legislative drivers creating legal pressure, explore technical detection methods, and help you determine the right approach for your business. Whether you're subject to age verification laws, geographic content restrictions, or contractual distribution agreements, this guide will help you navigate the complex landscape of VPN detection in 2026.

Failing to detect VPNs may violate local legislations
When the Online Safety Act came into force in the UK, overnight a surge of over 700% took place on the VPN search term.

Proton VPN reported a 1,400% jump in signups.

For a few weeks, this sudden surge was all over the news.
This inevitably triggered a counter response from legislators. The US state of Wisconsin was the first to react by Announcing Wisconsin Assembly Bill 105. The bill aims to force adult content sites to block VPN access.
The bill states: "A business entity that knowingly and intentionally publishes or distributes material harmful to minors on the Internet from a website that contains a substantial portion of such material shall prevent persons from accessing the website from an internet protocol address or internet protocol address range that is linked to or known to be a virtual private network system or virtual private network provider."
Under Louisiana’s Act 440, failing to verify age (such as allowing VPN access) opens the door to civil lawsuits. The parents of a minor that was able to access “harmful content” through a VPN can sue the site owner for damages, court costs and attorney fees.
Other US states like Michigan and Indiana are pursuing similar action. With Indiana pursuing legal action against over 50 websites.
In the UK, government officials are calling VPNs "a loophole that needs closing".
The conclusion here is clear: as a website owner it is your job to detect VPN traffic and prevent circumvention of age verification or state level blocks.
Failing to detect VPNs breaks contractual obligations on distribution rights
When content distributors purchase rights to certain content it is usually geographically limited. When users travel abroad VPN usage is commonly used to continue watching their favourite series from home.When users want to watch a series that is not available in their country, they frequently use a VPN to gain access to that content.
While the user mostly does this out of convenience, this is a breach of distribution rights and in 2026 it is growing increasingly common for film studios to enforce strict VPN prevention techniques to prevent breaches.
Why Age Verification Became A Legal Requirement
There has always been really 2 versions of the internet:
- The open, unauthenticated internet. Relatively anonymous with the exception of some tracking techniques.
- The authenticated internet. Users logging in with their credentials. They are known visitors and their access is conditional to them.
Over the years regulators identified that certain content types on the open and unauthenticated internet can be harmful at developing ages. This led to the legislation we see today, requiring companies to perform age verification on visitors.Age verification is currently being performed in a number of ways:
- Facial age estimation using Machine Learning.
- Credit Card Verification, to verify a user has a credit card, which means they are likely adults.
- Photo ID Verification
- Digital ID Wallets, sharing only an ‘over 18’ credential without further context
- Open Banking API to verify the age of the bank account holder
- Mobile Network Operator, allowing to verify the age of a visitor using the contract with the mobile provider.
- Email-Based estimation, verifying the email history of a user across the internet to estimate their age.
Some of these methods are seen as privacy intrusive and as a result website visitors end up using a VPN to work around the restriction instead of complying.
Ways to detect VPNs
There are a few methods that can be used to detect VPNs. Some are quick and dirty, others are more invested in being accurate.
1. Detections on the network and application level
Technical readers may be aware of the OSI stack. There are 7 layers of a network application in the OSI stack.

Across layer 3, 4 and 7 various elements differ between direct human connections and connections routed through VPN infrastructure. Investigating these layers yields evidence of VPN usage. For example - mismatching machine level timezones to claimed locations, or suspicious network packets.
An independent scientific review of VPN detection methods found this to be the most effective approach.
2. IP lists
A simple, quick approach is purchasing or obtaining an open-source list of IP addresses flagged as VPNs. This approach can cover some basic VPNs, but the cat and mouse game is often stronger. Internet users look for VPNs that don’t get flagged. VPN providers know when they get flagged and look for alternative measures. Using IP lists can be a start, it can show you made an effort to detect VPNs, but we fundamentally don’t believe this approach works in the real world.
If you really need to stop VPN access, you must be willing to face the fact that there are more people looking for ways around your detections than there are maintaining them. So a simple list of IP addresses will not pass the test of the real world.
Especially in a world where regulators have already shown intent to retaliate against checkbox oriented approaches, it’s best to recognize how an invested user will seek to bypass the detection efforts.
Tools to detect VPNs
With new age verification laws introduced in 2025 and 2026, companies are looking for ways to detect VPNs to prove that reasonable measures are in place. You can evaluate these solutions that offer rapid implementation:
cside VPN detection
cside detects VPN usage by inspecting network behavior and fingerprint signals which traditional web security tools miss. Specialized client-side visibility set this solution apart from other fingerprinting tools.
- Approach: Network and application level detection
- Use case: For companies under strict age verification laws that need to demonstrate compliance, cside offers advanced detection and evidence gathering to demonstrate adequate measures for regulators.
Fingerprint
Detects VPN and proxy usage with device, browser, and network behavior across sessions.
- Approach: Network and application level detection
- Use case: For security teams monitoring abuse patterns where users rotate IPs but reuse the same device or browser.
IPQualityScore
Maintains an updated databases of known VPNs, proxies, TOR exit nodes, and hosting providers.
- Approach: IP list
- Use case: Fast setup for VPN risk scoring using IP reputation.
MaxMind
GeoIP and Anonymous IP databases that flag VPNs and proxies.
- Approach: IP list
- Use case: Fast setup for VPN risk scoring using IP reputation.
How to respond to VPNs
Many websites may be tempted to simply block all requests from VPNs. While this would be easy to do, the issue is that it has become easy for a user to recognize they were caught. In some applications, blocking all VPN requests is the right approach. But in others, this will only trigger the user to look further for methods to avoid the detection.
In VPN detection along with bot detection it’s often better to customize the webpage response or make the webpages artificially slow to trigger the visitor to go elsewhere. In some cases, you may want to allow VPN traffic, but only if a user authenticates. That can be a fair compromise.
Not all VPN traffic is bad
VPNs are widely used by many users for legitimate cases:
- VPNs can be used to protect connections on public Wi-Fi
- Remote workers may be required to route traffic through corporate VPNs
- Travellers using VPNs to legitimately access the internet in a familiar environment (search results, language translations)
There is also the possibility of false positives picked up by detection tools. Aggressively blocking all VPN traffic can break functionality for benevolent users or harm customers. Age verification laws do not typically require outright blocking VPNs. They expect to see reasonable measures to protect audiences from harmful content.
What approach works best for you?
If your business is:
- subject to age verification laws
- subject to regional content restrictions
- subject to contractual agreements limiting distribution of media to specific geographies
Use cside’s VPN detection to handle the cat and mouse game. We’ll detect VPNs for you.
Conclusion
Implementing VPN detection may be a necessary task for your business to avoid liability, risk of fines and potential contract breaches. Use a solution that leverages deep fingerprints on the request level instead of IP lists.