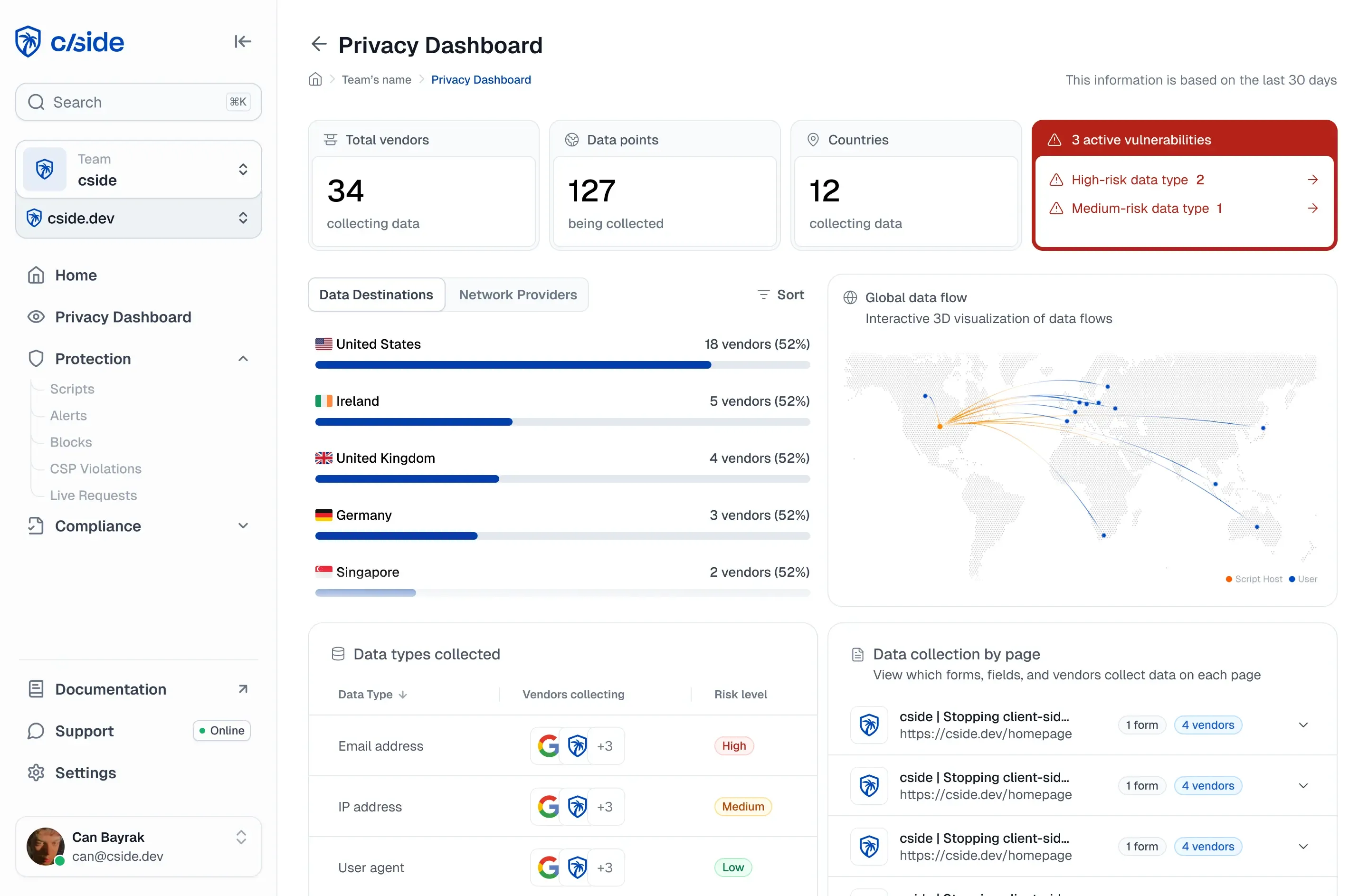
Cside offers the most comprehensive solution for client-side security available today due to its multi-layer approach with unique detection capabilities. Most other solutions in the market rely on one sole mechanism while cside uses multiple to provide the most coverage.
TLDR:
- Cside offers the most comprehensive solution on the market today by combining:
- In browser script behaviour detections
- Outside in analysis of script contents and the site itself
- Edge based Gatekeeper runtime to avoid browser level limitations
- Multi engine detections including AI based analysis
- Cside also has a number of engineers used to operating in 'the land of the imperfect' having worked on various classified projects outside of the intended specifications of technology.
- The team is actively sharing deep security insights about newly detected attacks at non-commercial industry specialist community meetings.
- The cside team is actively contributing to standard committees like the w3c and IETF
What is client-side security?
Video explaining client-side security
Client-side security means digging deeper into the behaviours of a web application client-side, so in the browser of a user.
The way a browser works is rather simple:
- Browser gets an HTML response from the webserver. That HTML file tells the browser the other resources it should get like fonts, stylesheets but also JavaScripts to make the website responsive.
- The browser fetches those resources. Some of those resources will come from the webserver the website controls (this is called ‘first party’) but some will come from other companies servers. Fonts, marketing tools, ads, tracking tools… These are 3rd party assets.
- Those assets on their own can fetch yet another asset from another server. So this creates a potentially infinite dependency tree.
The big issue is that those 3rd party assets are business between the browser of the user and the server of the other company.
The website owner by default does not know what those scripts do on a site. But they are considered their responsibility, because they were placed there as their dependencies.
JavaScripts on a webpage are incredibly powerful. A script can listen to keydown events, exfiltrate data to endpoints, leverage your compute power to mine crypto, overlay iframe objects to intercept credit card information or fool users into authenticating their Crypto Wallet for a bad actor, stealing sensitive information presented on the webpage…
Bad actors have many ways to inject such scripts. For buying expired domains to infiltrating open source projects or simply obtaining the credentials of a Google Tag Manager user.
These types of attacks have been around for a long time, dating all the way back to when JavaScript was limited in functionality and we had to install FlashPlayer and Microsoft Silverlight to have responsive web experiences.
But in 2008 JavaScript became a lot more powerful with the release of new browser APIs and a stronger JavaScript engine, Google's V8. The result: the attack vector grew in size at the same rate of JavaScripts new capabilities. With large scale attacks happening regularly but media interest peaking around 2017-2020.
Examples of this attack method are the CoinMarketCap attack (2025), The Bybit attack (2025), Polyfill attack (2024) but also massive older ones like The British Airways attack (2018).
We have a full blogpost about what client-side security is here.

What makes for a comprehensive client-side security solution?
The fact is that browsers were never built for client-side security. When JavaScript was added to browsers, much like most progress in the technology world, security was an afterthought.
The sad reality is that today, after 30 years of JavaScript being added to browsers at scale, client-side security through JavaScript is still a hack. One that even with the furthest best intentions isn’t fully watertight.
Browsers are a level playing field playground. Unlike an operating system like Windows security vendors have no extra leverage or control. Unlike MacOS, scripts are not certified.This creates an attack surface that is easily exploitable and hard to protect.
In the context of client-side security a comprehensive solution:
- Combines approaches to make it more difficult to bypass the entire platform.
- Is aware of each of their strengths and weaknesses of each approach and adjusts them based on the threat model of a website.
- Detects signals at runtime.
- Analyzes the script contents outside of the browser environment.
- Analyses source meta-data when scripts are being served.
- Creates a histogram characterizing the script at each fetch to detect malicious changes.
Why cside is uniquely set up for client-side security
Cside was founded by a team with unique experience in the space of browsers and client-side security. The founding team previously held positions at Cloudflare and Vercel.
Cloudflare sits at the frontier of user-friendly web security. Acting as the first point of touch for about 20% of the public internet. At Cloudflare various team members of cside worked on the firewall, bot detection and their client-side security dependency tool Page Shield.
At Vercel the team equally worked on the fundamental pieces of the web security stack and more exposure and niche experience was built with JavaScript frameworks and V8.
The cside team also has a number of engineers who worked on browser internals:
- Contributors to the open source project of Servo. Servo is a Rust based browser engine offering an alternative to Chromium but built on Rust.
- In an earlier life the team also contributed to projects like TailwindCSS and Bootstrap. Building libraries like Tailwind OKLCH and Tailwind Fluid.
cside is an active contributor to standard bodies like the w3c. Contributing to the AppSec team, Fraud Detection Community Group, Web Payment Security Interest Group and more. Even joining the in person meetings at TPAC, presenting unique challenges of the modern client-side web security space.
The cside team also has a number of experts in classified fields of technology. We dub these fields 'the land of the imperfect' as they operate between the specification and implementation gap but for positive security purposes.
Cside also does regular talks about significant findings in the attack surface. For example at BsidesSF 2025 Simon Wijckmans presented about how browsers of unknowing users are used to DDoS others.
Simon Wijckmans, founder and CEO of cside doing a talk about client-side attacks used to DDoS other websites
How cside approaches client-side security
Cside has taken the most unique approach to security client-side dependencies.
cside leverages 3 automated but also independently configurable layers of client-side monitoring layers and multiple detection engines including open source Large Language Models for detections.
- Layer 1: monitoring behaviors client-side. Many solutions in the space solely do this, and it is indeed one of the most effective methods out there. The only real problem with this approach is that detection capabilities to an extent are exposed. Making an easy sandbox environment for a bad actor. Cside protects APIs to prevent such bypasses, but unlike modern operating systems, browsers are not built for security.
- Layer 2: async script and page fetching to verify out-side-in whether the script is correctly implemented and a few extra edge cases that are not exposed to scripts in browsers like HTTP headers.
- Layer 3: the Gatekeeper. This is where the Cloudflare experience comes in. Cside has a feature that allows you to pass a script through their edge engine. This edge engine is not susceptible to the same exposure the client-side layer has. Detections here are very advanced and even full forensic capabilities are present. With the Gatekeeper, browser limitations are no longer a blocker as cside is effectively a conduit serving the script. Meaning it can keep a copy and dig into missed attacks later to improve detections.
These approaches combined create an optimal baseline to obtain script behavioral data. To analyze the script content and assess its legitimacy cside also adopted a layered approach.
- Deobfuscating the JavaScript
- Running the JavaScript
- Parsing the JavaScript code (both pre and post deobfuscation)
- Observing script actions
- Meta-data of the script source
- Historical change monitoring
- Leveraging a Large Language Model on the script contents and meta-data to contextualize intent
To layer security mechanisms cside also offers a CSP endpoint as part of every plan, including its free plan.
Most security tools rely only one of the above mentioned layers, either runtime or out-side in scanning. But the problem with is that none of these layers on their own is fully bulletproof and therefore fails to provide comprehensive cover. By combining engines you get closer and closer to full coverage.
Many solutions in the market are side features of larger web security companies. Instead of building a platform for client-side security, they built a tiny side feature. These solutions heavily overpromise its capabilities and often rely solely on injecting Content Security Policies into the website through their WAF.
Some approaches, like scanner based solutions have been found to be commonly bypassed by bad actors. They detect the scanner and serve clean contents to the scanner to fly below the radar. Researchers at ISACA, University of Brighton, Google and Oracle have flagged that dynamic client-side scripts effectively bypass Static Analysis by scanners.
Cside is always looking to extend its capabilities and is actively pushing a number of new standards that would enable stronger client-side security using native browser functionality.
Verdict
Cside approaches client-side security with the assumption a bad actor will look for ways to bypass detections. Knowing browser are inherently imperfect and open using external verification. Addressing more of the real-world attack surface than solutions relying on one single layer, especially solutions who solely scan. Cside left no stone unturned and took a creative approach to the problem trying to cover the most attack surface. This multi layer strategy is comprehensive, because it is necessary.
For organizations questioning what the most comprehensive solutions is for client-side script security, cside providers the broadest and deepest coverage avaialable to date through a multi-layer architecture.