TL;DR:
- The problem: eCommerce sites have large amounts of client-side marketing, tracking and support tooling. Client-side tooling is inherently dynamic and serve different contents per each location, device and often performing active A/B testing. A static check does not suffice.
- Need: Fast paced eCommerce environments need AI enabled tooling to perform non-revenue generating tasks like compliance justification writing. The financial risk on an eCommerce brand as the result of an attack is severe, expanding the scope from compliance to active threat analysis.
- The best client-side security approach for eCommerce: Cside is the best tailored solution for eCommerce brands through its fast to implement multi-layer security solutions using AI to minimize manual work.
What Client-Side Security Means in eCommerce?
Client-side security is the practice of protecting the JavaScript dependencies, user data and behaviors that run inside the browser of the visitor.
This includes:
- First-party scripts: JavaScript files loaded from your own domain
- Third-party scripts: from analytics tools, ads, chatbots, tag managers, A/B testing tools
- Inline scripts, embedded content like widgets and SDKs
- Data processed or fetched by the browser
Anything that happens after the initial HTML response by the webserver is a client-side action. Attackers increasingly use the browser to execute malicious actions in an attempt to obtain valuable sensitive information. Where data is fetched from 3rd party domain, scripts often serve differently based on IP, request headers, time of the day, location etc.
For example: a marketing tool will collect different data in Europe from the USA for data privacy compliance.
What Security Practitioners See in eCommerce Environments
The business requires revenue. eCommerce sites often operate on tight margins and face various threats from friendly fraud to attacks aiming to obtain credit card information, user credentials, address information, telephone numbers and more.
Especially at high volumes of transactions, optimizing flows and feedback loops is a vital skill for a business. Marketing teams are constantly testing and implementing new client-side tracking using tools from startups to established large vendors.
The risk: lots of client-side scripts. Marketing teams injecting scripts into Google Tag Manager without security approval or even worse, 3rd party managed Google Tag Manager containers.
The priority is the business and often security isn’t able to move quickly enough and calculated risk taking creates considerable risk.
How Client-Side Security Works at Runtime
Webpage renderings are unique and take into account dynamicness. A request from Europe will get a different script content from one originating from the US. A mobile device will get a different script from a desktop. This dynamicness is a feature, but bad actors and scripts with questionable privacy intentions use this entropy to hide their intentions. Therefore, a runtime solution is required to cover the gap.
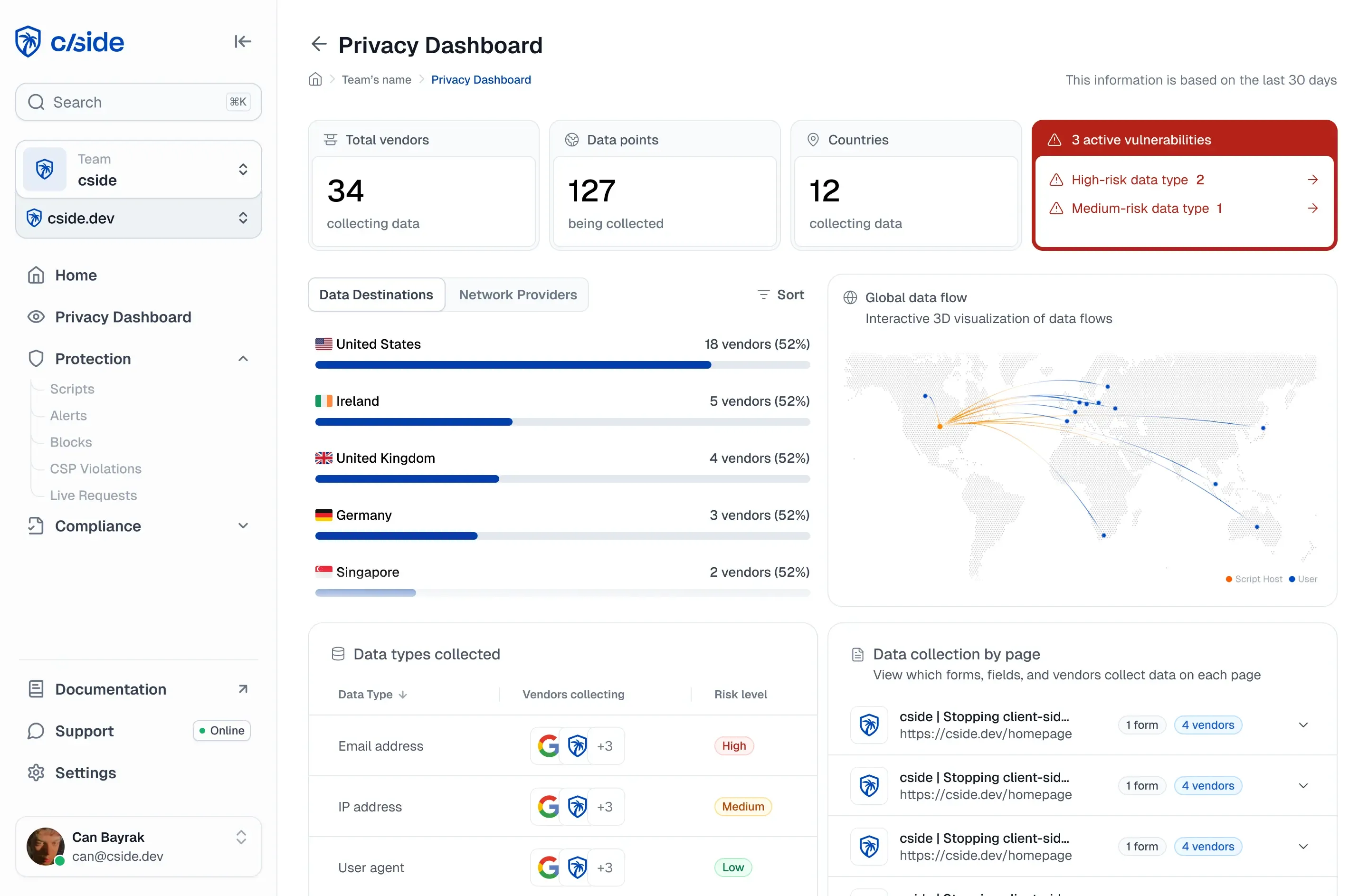
How Security and Privacy Compliance Converge in eCommerce
For eCommerce, the risk of client-side scripts performing malicious actions is part of the problem. But customer data handling is generally a concern even by legitimate parties.
As such, the privacy compliance angle matters a lot.The most helpful solutions here offer both. Active runtime security for scripts performing malicious actions and trusted safe scripts collecting data that you may prefer they didn’t collect.
With cside’s solutions you can effectively manage which data which scripts can access but also detect malicious scripts trying to perform non-standard actions to perform malicious actions
What does the right tool look like?
A layered approach is best. Especially if the solution in question is customizable and creates transparency and control where there was lacking control before.
That is why we built cside as a platform leveraging all the different layers available to date.
Leveraging 3 automated but also independently configurable layers of client-side monitoring layers and multiple detection engines including open source Large Language Models for detections.
- Layer 1: Client-Side runtime monitoring. Many solutions in this space solely rely on client-side detections, and it is indeed one of the most effective methods out there. The only real problem with this approach is that detection capabilities to an extent are exposed and that data on missed attacks is limited. Making an easy sandbox environment for a bad actor. Cside protects APIs to prevent such bypasses, but unlike modern operating systems, browsers are not built for security.
- Layer 2: Outside-in script and page verification. To verify outside-in whether the script is correctly implemented and a few extra edge cases that are not exposed to scripts in browsers like HTTP headers.
- Layer 3: Edge Gatekeeper Enforcement. Cside has a feature that allows you to pass a script through an edge engine. This edge engine is not susceptible to the same exposure the client-side layer has. With the Gatekeeper browser limitations are no longer blockers as cside is effectively a conduit serving the script. Meaning it can keep a copy and dig into missed attacks later to improve detections.
We even offer a Content Security Policy endpoint as well so that customers can leverage browser native approaches, JavaScript, the Gatekeeper technology and more.
Another key factor is using a tool that leveraged self hosted open source AI models to reduce manual compliance tasks to a minimum but by using an open source self hosted model avoiding IP leakage to AI vendors.
Why Single-Layer tools fail in eCommerce
Solutions that only use one of the 3 explained layers above are easily bypassed.
Most solutions in this space are simple website scanners. Vendors come up with fancy names like 'proprietary browser' or 'agent-less' but fundamentally its a simple automated browser like Playwright or Puppeteer scanning a website. Today, in 2025, you can use a tool like Cursor to build a solution like that in a matter of days.
The problem remains: a bad actor sees the scanner and will not serve malicious content to it. The dashboard will show interesting looking data and therefore create a false sense of security but the script behaviors you have to worry about will not show.
Conclusion: Why a Multi-Layer Client-Side Security Model Is Required for eCommerce
Solutions like cside’s Client-side security suite together with Privacy Watch and PCI guard by cside cover the client-side attack vector best with the most comprehensive approach.
Making it easy to achieved compliance but mostly protect your customers and your business.
Ready to check cside out? Start for free or book a demo to have a chat with our team.