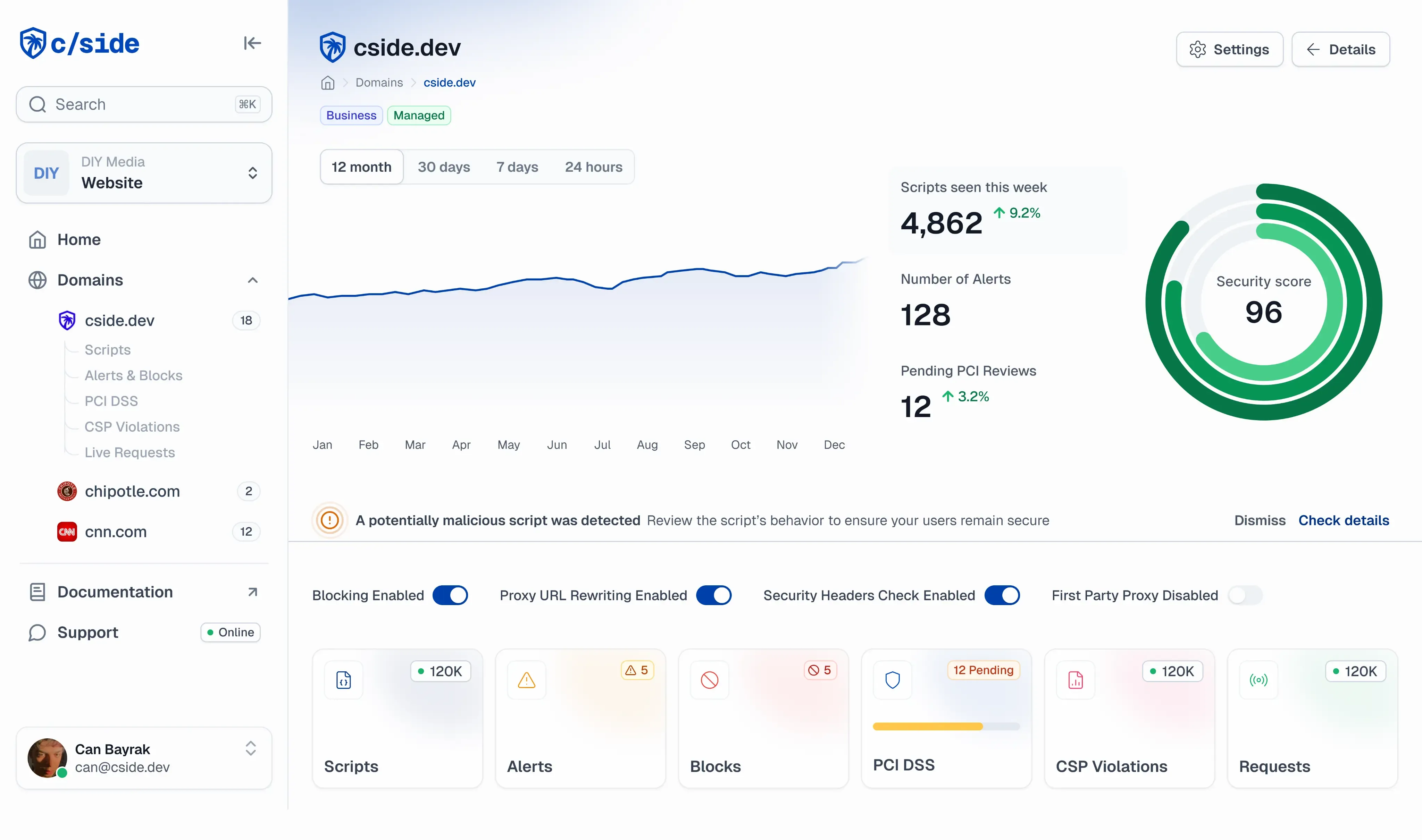
Monitor the Scripts That Cause the Most Risk
Every time your user or visitor loads your website or web application, they don't only load components from you, but also components from the wider web and third-party vendors. You only have visibility on what is happening server-side, not what is actually being loaded into the user's web browser.