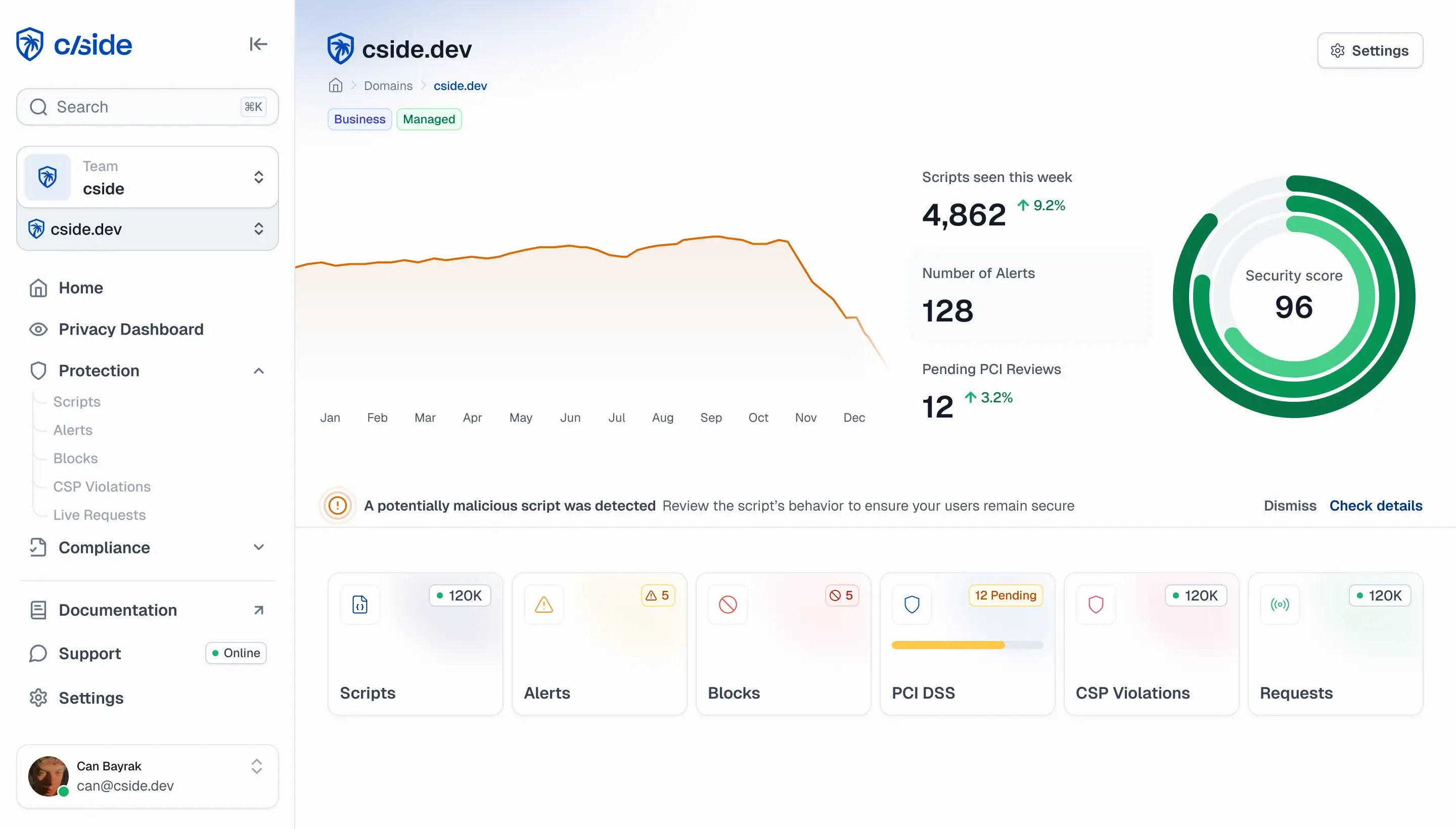
cside's architecture provides comprehensive client-side protection specifically designed for the unique challenges of eCommerce checkout flows.
Your Checkout Page Is the Target
Credit card skimming happens in the browser where traditional security tools can't see it. By the time you discover a breach, thousands of cards may be compromised.
Marketing tags, analytics, chatbots, and payment widgets all execute in the browser. A compromise in any one of these can lead to a massive data breach.
Requirements 6.4.3 and 11.6.1 mandate script integrity monitoring and authorization of all scripts on payment pages. CSPs and manual audits aren't enough. Learn more about PCI DSS compliance.
cside's architecture provides comprehensive client-side protection specifically designed for the unique challenges of eCommerce checkout flows.

cside monitors the activity of every script, preventing malicious code from stealing payment or customer data.
PCI 6.4.3 & 11.6.1 requirements with script inventory, change detection, justifications, and audit-ready reports.
Reduce friendly fraud (chargebacks) with device fingerprinting as evidence to block disputes.
Payment pages handle credit card data
High-value customer data (addresses, phone numbers, and purchase history)
Checkout flows have multiple third-party dependencies
Seasonal traffic spikes mask malicious activity
Modern web apps load more code in the browser, widening the attack surface.
"Client-side security was a blind spot for us until we implemented cside. Now we have complete visibility into our third-party scripts and can prevent data breaches before they happen."
Discover how cside can help you secure your eCommerce platform and protect your customers' payment data.
Common Client-Side Attacks on eCommerce Sites
Code injected into checkout pages intercept credit card data, CVV numbers, and customer information
Attackers purchase expired domains of scripts on your site to change code from an approved source.
A breach in one of your trusted providers (analytics, chatbots, marketing tool) can compromise your entire checkout flow.
Advanced Magecart variants target specific sessions (high-value orders, certain geographies) to evade detection.
Malicious scripts copy form data including payment details and send it to attacker-controlled servers
Attackers steal session tokens to impersonate customers and make fraudulent purchases
cside delivers advantages traditional tools can't match.
| vs. Crawler-Based Solutions | vs. Content-Security Policy (CSP) | vs. Client-Side Agents |
|---|---|---|
| Sees real user behavior, not sanitized crawler views | Monitors script payloads, not just sources | Undetectable monitoring attackers can't bypass |
| Catches attacks aimed at specific segments | Detects breaches at trusted third-party providers | Complete historical script behavior tracking |
| Detects threats between periodic scans | Handles dynamic scripts CSPs can't control | Future-proof against evolving techniques |
Cside directly addresses PCI DSS requirements 6.4.3 and 11.6.1 in a purposely built dashboard addressing the specific requirements line by line. Offering automated monitoring and authorization of the scripts interacting with payment forms. We give you the visibility and control that auditors require. Cside has even been validated by VikingCloud, one of highest reputation QSA firms in the industry.
Cside monitors all JavaScript execution on your site and detects when scripts attempt to access form fields related to sensitive data such as Payment Card Data, PII or PHI or exfiltrate data to external endpoints. We notify of alarming behaviours and block malicious actions before customer data is compromised.
It wouldn't. In fact, depending on the page we may even make the experience faster. cside's architecture is designed for minimal performance impact. The script-based monitoring approach has no impact on performance. Most merchants see no difference in page load times after deployment.