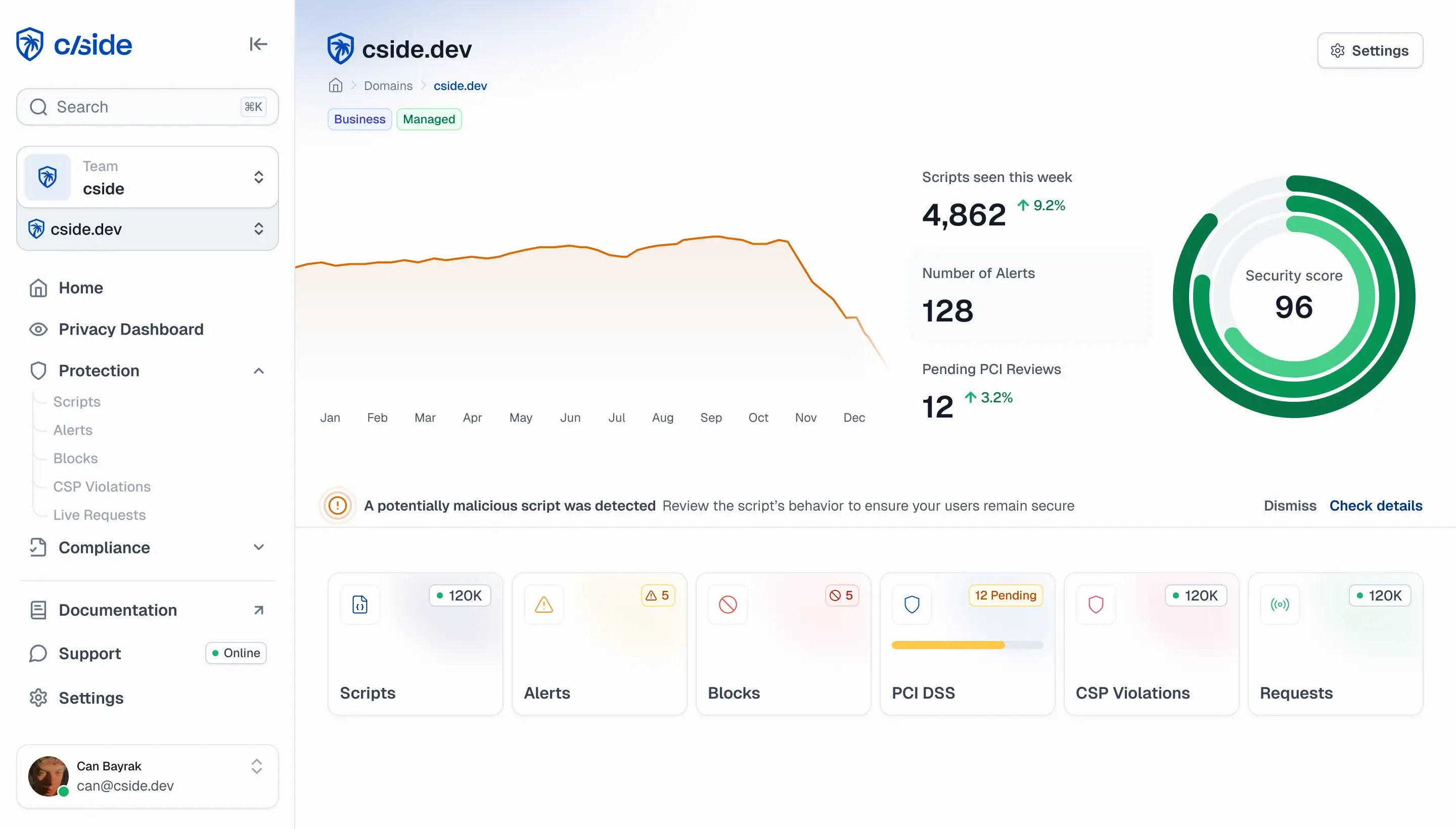
cside's architecture provides comprehensive client-side protection that extends from your payment gateway to every merchant checkout page.
Your Merchant's Checkout Pages Are the Target
Merchant websites load dozens of 3rd party scripts (marketing tags, data integrations, analytics). One bad script exposes their customers to payment card skimming.
Even when using payment iframes, the parent page can be compromised. Attackers intercept data before it reaches your secure iframe or steal authentication tokens.
Requirement 6.4.3 and 11.6.1 mandate that scripts on payment pages are authorized, monitored, and have script integrity checks. Traditional tools don't provide this visibility.
cside's architecture provides comprehensive client-side protection that extends from your payment gateway to every merchant checkout page.

Payment pages handle credit card data
High-value customer data (addresses, phone numbers, and purchase history)
One successful script exploit can be repeated across different merchants
Modern web apps load more code in the browser, widening the attack surface.
"cside's real-time monitoring and threat detection capabilities have been crucial in maintaining our PCI DSS compliance and protecting our customers' payment data."
Learn how cside can help you secure your payment processing platform and maintain compliance.
Common Client-Side Attacks on Payment Pages
Code hidden on merchant checkout pages intercept payment card data before it reaches your payment gateway
Attackers purchase expired domains of scripts on merchant sites to change code from an approved source.
A breach in one of the merchant's trusted providers (analytics, chatbots, marketing tool) can compromise the entire checkout flow.
Advanced Magecart variants target sessions with specific criteria (e.g. IP address, time of day) to evade traditional detection.
Malicious scripts steal session tokens and authentication cookies to impersonate legitimate payment requests
Attackers inject code that copies form data (including CVV and card numbers) and exfiltrates it to attacker-controlled servers
cside delivers advantages traditional tools can't match.
| vs. Crawler-Based Solutions | vs. Content-Security Policy (CSP) | vs. Client-Side Agents |
|---|---|---|
| Sees real user behavior, not sanitized crawler views | Monitors script payloads, not just sources | Undetectable monitoring attackers can't bypass |
| Catches attacks aimed at specific segments | Detects breaches at trusted third-party providers | Complete historical script behavior tracking |
| Detects threats between periodic scans | Handles dynamic scripts CSPs can't control | Future-proof against evolving techniques |
The protection you get from cside is extended from your payment gateway to every merchant checkout page. All scripts loaded on merchant sites are monitored, giving us the capability to detect malicious behaviour even before they can compromise payment data.
The answer is yes. We help merchants take ownership of their client-side security by providing merchant-facing dashboards that allow them to see their script inventory, security alerts, and compliance status.
Cside helps payment providers and merchants reduce chargebacks and win disputes with our card-not-present fraud prevention and by providing forensic evidence of legitimate transactions.