PCI Compliance 4.0.1: A Practical Implementation Guide Webinar
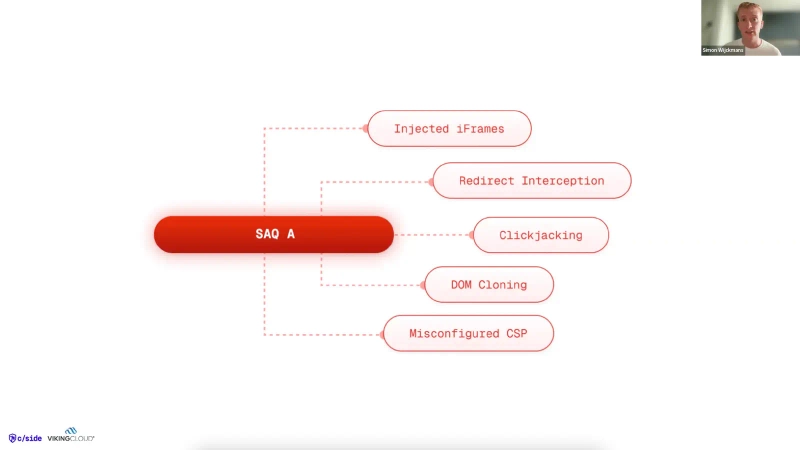
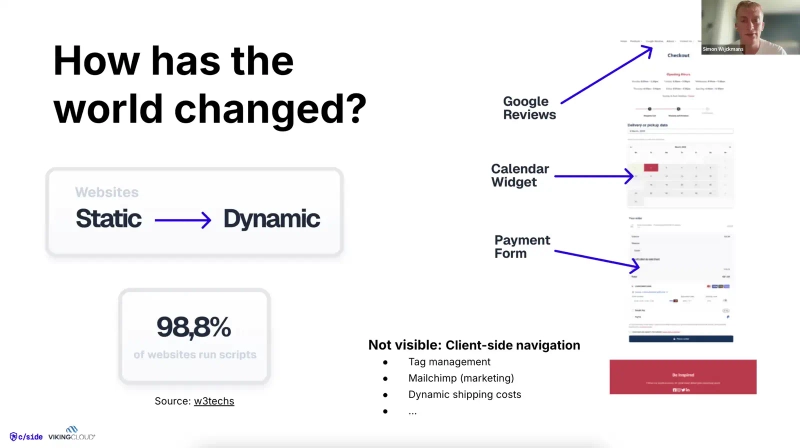
We partnered up with VikingCloud, the largest global PCI compliance and security firm on 4 continents giving you the full context and info to implement PCI DSS 4.0.1. With a special focus on requirements 6.4.3 & 11.6.1.
Hosted By:


Watch the Recording
Fill out the form below to be redirected to the recording.