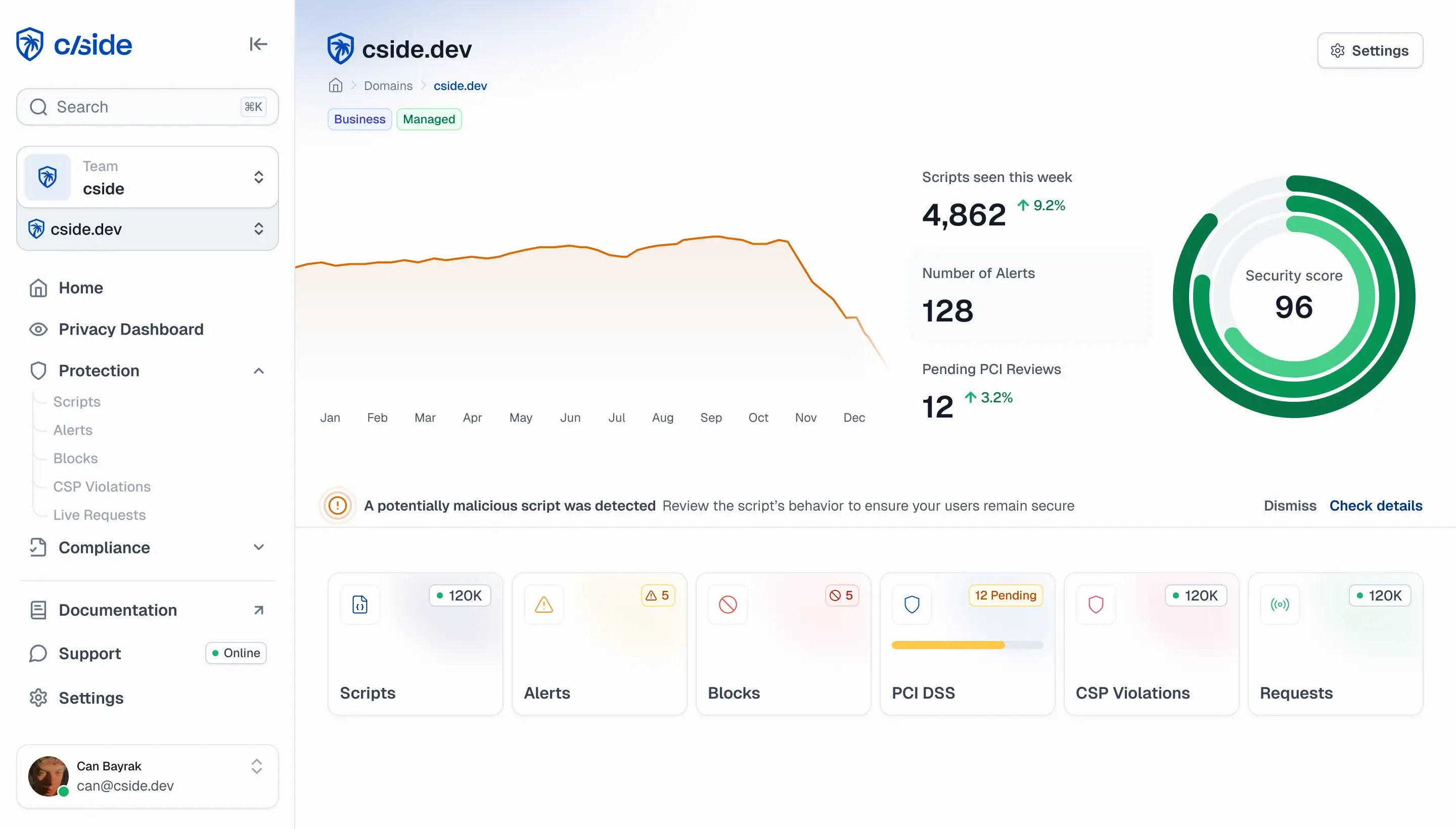
cside's architecture provides comprehensive client-side protection specifically designed for the unique challenges of hospitality and hotel booking platforms.
Your Guest's Browsers Are the Target
Your website loads dozens of 3rd party scripts (marketing tags, data integrations, analytics). One bad script exposes your guests to attacks.
Fraud tools and separate payment portals don't monitor the browser. CSPs and crawlers are evaded by attacks with dynamic JavaScript.
Hospitality & hotel platforms fall under PCI DSS, GDPR, and regional data laws that hold organisations accountable for 3rd party scripts.
cside's architecture provides comprehensive client-side protection specifically designed for the unique challenges of hospitality and hotel booking platforms.

Our proxy monitors the activity of every script, blocking malicious code from reaching users on your platform.
PCI 6.4.3 & 11.6.1 requirements with script inventory, change detection, justifications, and audit-ready reports.
Identify what personal data each third-party script has access to and where it's sent. Stay compliant with GDPR + HIPAA by preventing PII leaks.
Our system creates device fingerprints for every user session, enabling detection of suspicious activity from bots or humans at the browser level.
High value data: Guest ID scans and card details are prime targets for attackers.
Multiple "trusted" scripts: marketing tags, chatbots, code libraries, and script tag managers are all entry points for browser attacks.
Easy to hide: Reservation and payment flows already collect sensitive data that attackers want.
Apps run client-side: Most bookings take place on a desktop or mobile browser, widening the attack surface beyond your servers.
"Guest data security is paramount in hospitality. cside helps us maintain trust by ensuring every script on our booking platform is secure."
See how cside can help you protect your hospitality platform and guest data.
Common Client-Side Attacks on Hospitality & Hotel Platforms
Code hidden on booking or payment pages steal card data and personal information
Attackers purchase expired domains of scripts on your site to change code from an approved source.
A breach in one of your trusted providers (analytics, chatbots, marketing tool) infects your entire site.
Advanced threats target sessions with specific criteria (e.g. IP address) to evade traditional detection.
Unmonitored scripts exfiltrate sensitive guest information such as passport data and stay details
Injected ads or pop-ups inside the browser trick guests into clicking fraudulent booking links
Don't Wait for a Data Breach or Audit Failure
cside tells me everything I need to know about a script, and makes sure they are safe to show to the user. It's really made me realize how big of a problem 3rd party script security is, and there are no other solutions I've tried that dive as deep as cside.Joseph M
Software Engineer
cside monitors all scripts on your booking platform and detects when guest data (payment details, personal information, stay details) is accessed by unauthorized scripts. We block malicious activity in real-time.
Yes. cside protects all pages where sensitive guest data is displayed or entered, including loyalty program dashboards, account management, and booking history pages.
cside monitors web-based interfaces and integrations with property management systems to ensure that guest data is not leaked through client-side scripts.