HIPAA Compliance Made Simple with Client-Side Security
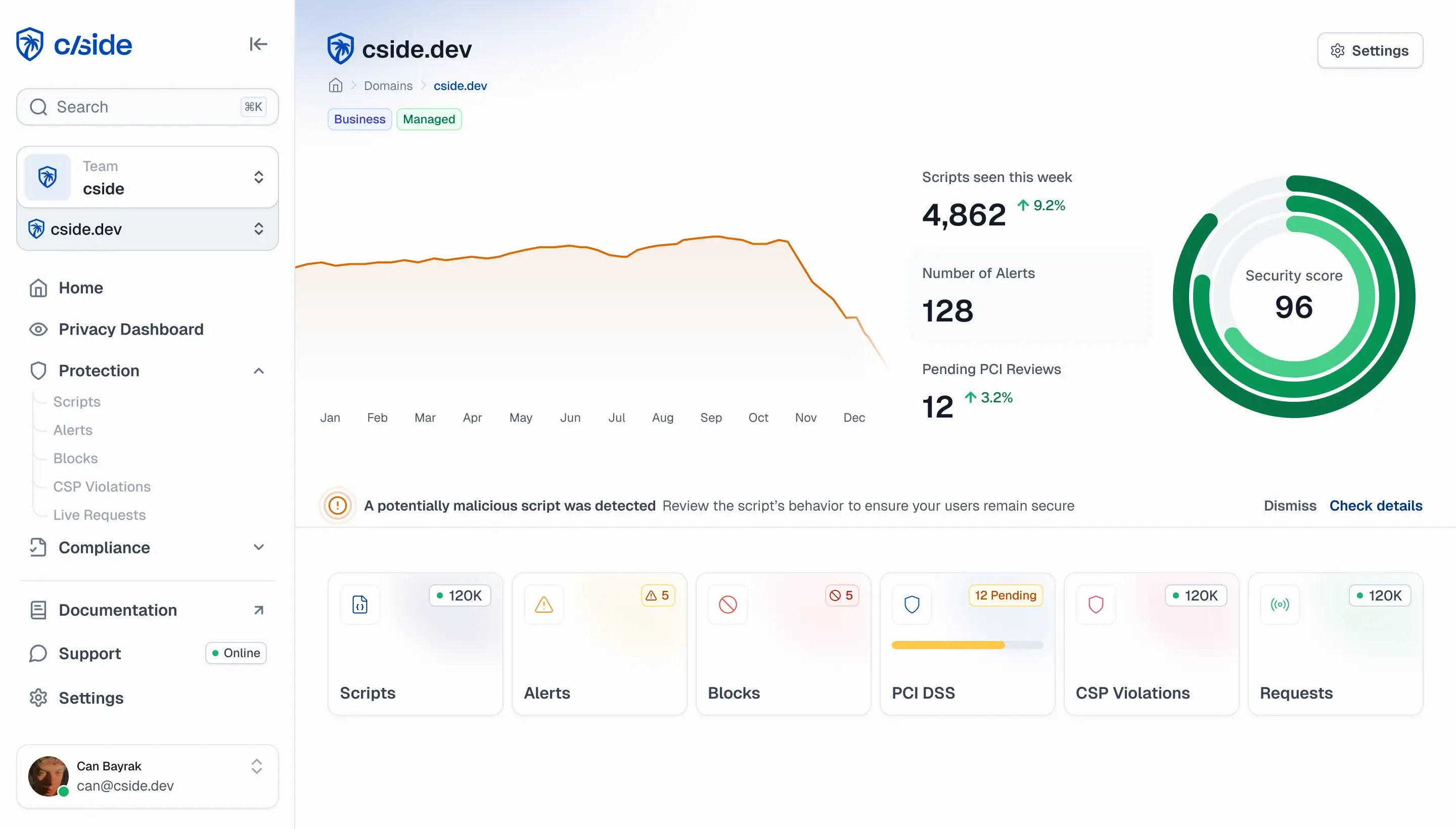
Keeping PHI safe client-side. The Health Insurance Portability and Accountability Act (HIPAA) protects U.S. health information. A major compliance issue comes from third-party tracking cookies, because they can send PHI to outside vendors without a Business Associate Agreement (BAA) or authorization. With protected health information (PHI) entering through browsers and mobile apps, server-side controls aren't enough. You need client-side visibility and control. cside delivers both and adds audit-ready evidence.