cside's architecture provides comprehensive client-side protection specifically designed for the unique threats facing crypto and DeFi platforms.
Your User's Browser Is Where Funds Are Lost
Interception of wallet connections, modification of transaction parameters, or theft of private keys directly from the browser are some of the things that malicious scripts can do. Oftentimes, when users start noticing suspicious activities, their funds are already gone.
Modern websites use numerous third-party scripts for analytics, price feeds, widgets, and marketing tools. One thing they all share in common is the fact that they execute JavaScript in your users' browsers. Bad actors only need to compromise one dependency to wreak havoc on your entire platform.
Some attacks are designed to evade traditional security tools to target high-value transactions. Think of attacks on npm packages, CDNs, and even wallet SDKs to inject malicious code.
Regardless if the attack came from a third-party script, you will still find yourself being blamed for a security breach on your platform, especially if users lose funds. Both your reputation and user trust are at stake.
cside's architecture provides comprehensive client-side protection specifically designed for the unique threats facing crypto and DeFi platforms.

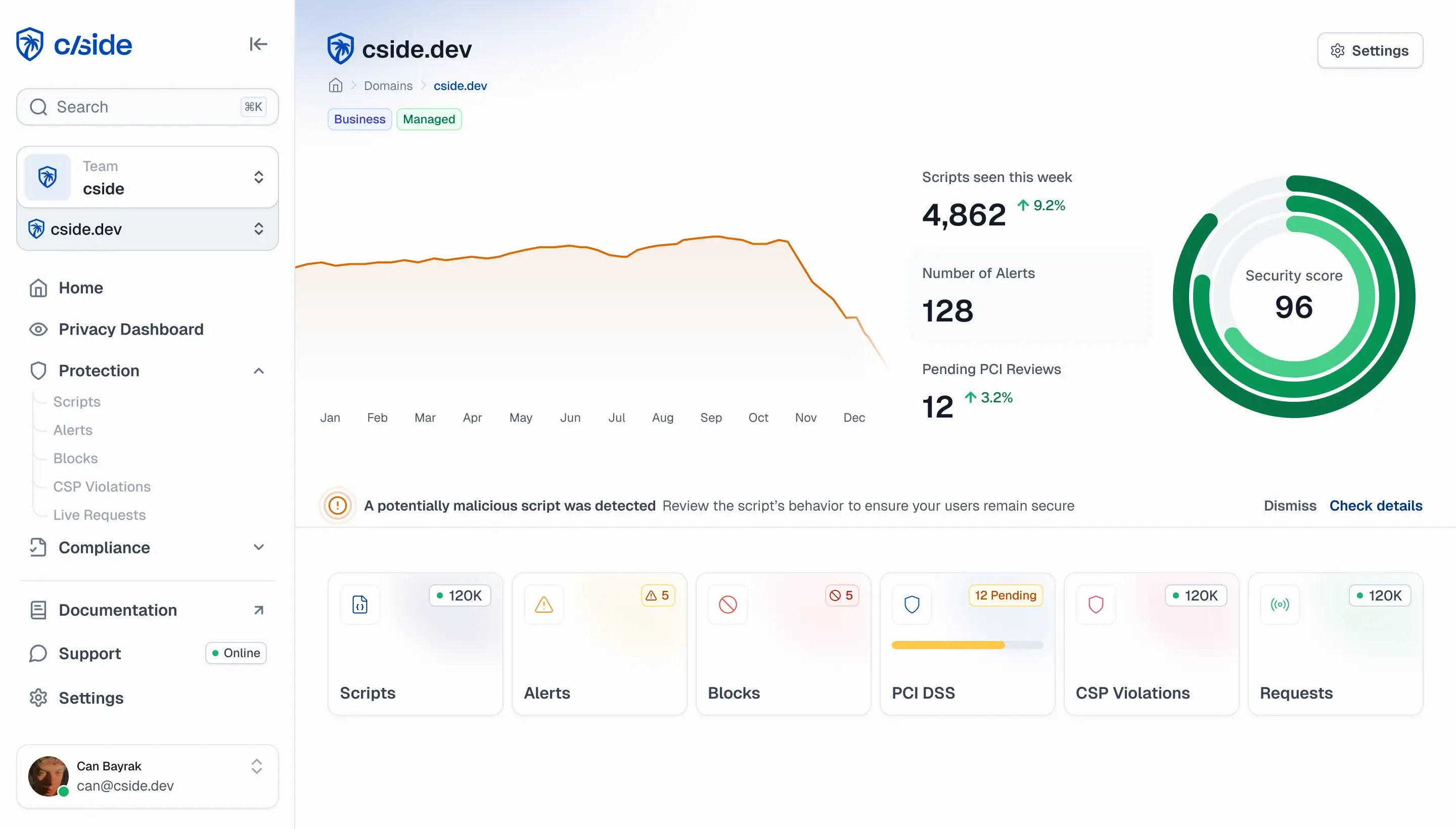
cside monitors the activity of every script, preventing malicious code from stealing wallet or payment data.
PCI 6.4.3 & 11.6.1 requirements with script inventory, change detection, justifications, and audit-ready reports.
Identify what personal data each third-party script has access to and where it's sent. Stay compliant with GDPR and prevent PII leaks.
Reduce friendly fraud (chargebacks) with device fingerprinting as evidence to block disputes.
High value transactions make every compromised browser session a lucrative target
Registration flows KYC and personal data that can be harvested
Third party services (trading widgets, analytics, integrations) expand the attack surface
Client-side scripts often touch wallet IDs, private keys, and addresses
"cside tells me everything I need to know about a script, and makes sure they are safe to show to the user. It's really made me realize how big of a problem 3rd party script security is, and there are no other solutions I've tried that dive as deep as cside."
Our experts can conduct a client-side vulnerability assessment and show you how to protect your crypto platform from client-side attacks.
Common Client-Side Attacks on Crypto Platforms
These are scripts that can intercept wallet connections and drain funds. They can do this by either modifying transaction parameters or stealing private keys.
There are malicious code that can change recipient addresses, amounts, or smart contract interactions in real-time.
Malicious codes are injected into your dApp through compromised npm packages, wallet SDKs, or Web3 libraries.
Your copied wallet addresses can be replaced with attacker-controlled addresses if a malicious code is set to monitor your clipboard.
Unauthorized access to user accounts and trading capabilities can happen when attackers steal your session tokens.
Injected fake wallet connection prompts or approval requests on your page can trick users into signing malicious transactions.
cside delivers advantages traditional tools can't match.
| vs. Crawler-Based Solutions | vs. Content-Security Policy (CSP) | vs. Client-Side Agents |
|---|---|---|
| Sees real user behavior, not sanitized crawler views | Monitors script payloads, not just sources | Undetectable monitoring attackers can't bypass |
| Catches attacks aimed at specific segments | Detects breaches at trusted third-party providers | Complete historical script behavior tracking |
| Detects threats between periodic scans | Handles dynamic scripts CSPs can't control | Future-proof against evolving techniques |
We monitor all JavaScript execution in real-time and detect any attempt to access wallet APIs or modify transaction parameters. Malicious patterns are identified using our behavioral analysis, preventing funds from being stolen.
The answer is yes. We track every script loaded on your platform. This includes npm packages and Web3 SDKs. We can immediately detect a compromised dependency as malicious behavior and block it before it reaches users.
We work with all major wallet providers. This includes MetaMask, WalletConnect, Coinbase, and others. Browser-level interactions are monitored, regardless of which wallet your users choose.